Cybercrimes target both individuals and businesses. The results of cyber-hacking can be as minor as a pesky popup that has to be removed by your IT department to malware that destroys your entire organization’s ability to do business. Cyber hackers can steal data, hijack and hold ransom entire software systems or break-in and alter files, using legitimate devices to lure others into revealing sensitive information, or worse, send money at the behest of a trusted fellow employee. Whatever the scope of the attack, cyber threats affect everything from productivity to data to credibility with your customers. Protecting against Cybercrimes should be a priority for every business, however large or small.
DOWNLOAD THE CYBER LIABILITY GUIDE
Please share your email to download
Before a Cyber Attack
The right controls, internal checks, and protocols can stop an attack before it starts. Here are 6 things you can do to protect your company BEFORE a cyber incident occurs:
- Connect to the internet over secure, password-protected networks: this means every employee working from home needs access to a VPN.
- Be suspicious of, and immediately discard, emails from unknown sources or those with attachments that are not logical.
- Look at the sender email carefully: just because the name sounds familiar doesn’t mean it is actually from that person.
- Type a URL by hand instead of clicking a link.
- Legitimate organizations never ask for your PIN, password, or other personally identifiable information. If it seems like it’s coming from IT, call over to the person you know and ask if it is them (it’s not).
- Even smart people fall for scams, be vigilant, logical, and ask other people if you have doubts.
During a Cyber Attack
If all your company’s vigilance has not protected you and you are a victim of a cyber attack, the actions you take upon uncovering the incursion are crucial. The first step you must take is to disconnect your device from the internet and perform a full system restore. Your cyber liability will be must better confined to only the infected machine by taking this first, important step.
Actions You Can Take to Limit the Damage:
Disconnect your devices from the internet. Hackers use the connection to the internet’s vulnerabilities to gain access to your machine, and then, through your machine, possibly gain access to other systems to which you are connected. By disconnecting your machine from the internet you quarantine your computer, preventing the spread of the hack beyond your machine.
- Update anti-virus software.
- Perform a scan of your entire system.
- Install all of the appropriate patches to fix known vulnerabilities.
- Notify your company’s IT department immediately.
You may have unknowingly revealed sensitive information about your organization. Alert the appropriate people within the organization, so that they can be on the lookout for suspicious or unusual activity.
After a Cyber Attack
Corporate Cyber Security Protocols will vary slightly between organizations. If your organization does not have a Cyber Security Protocol, the recent attack will likely spur that action internally. If you have addressed the vulnerabilities and are certain that the threat has been contained, the final steps are to:
- Alert the authorities. Let local police know so that there will be an incident report. Patterns can emerge and authoritiesdedicate resources to uncovering local, national and international hacking cels. Your report is part of a larger picture.
- Report online crime or fraud to the Internet Crime Compliance Center (IC3) or the federal government’s internet fraud resource website.
- Report identity theft to the Federal Trade Commission.
If your Personally Identifiable Information (PII) was compromised, take action to ensure that your identity is not stolen.
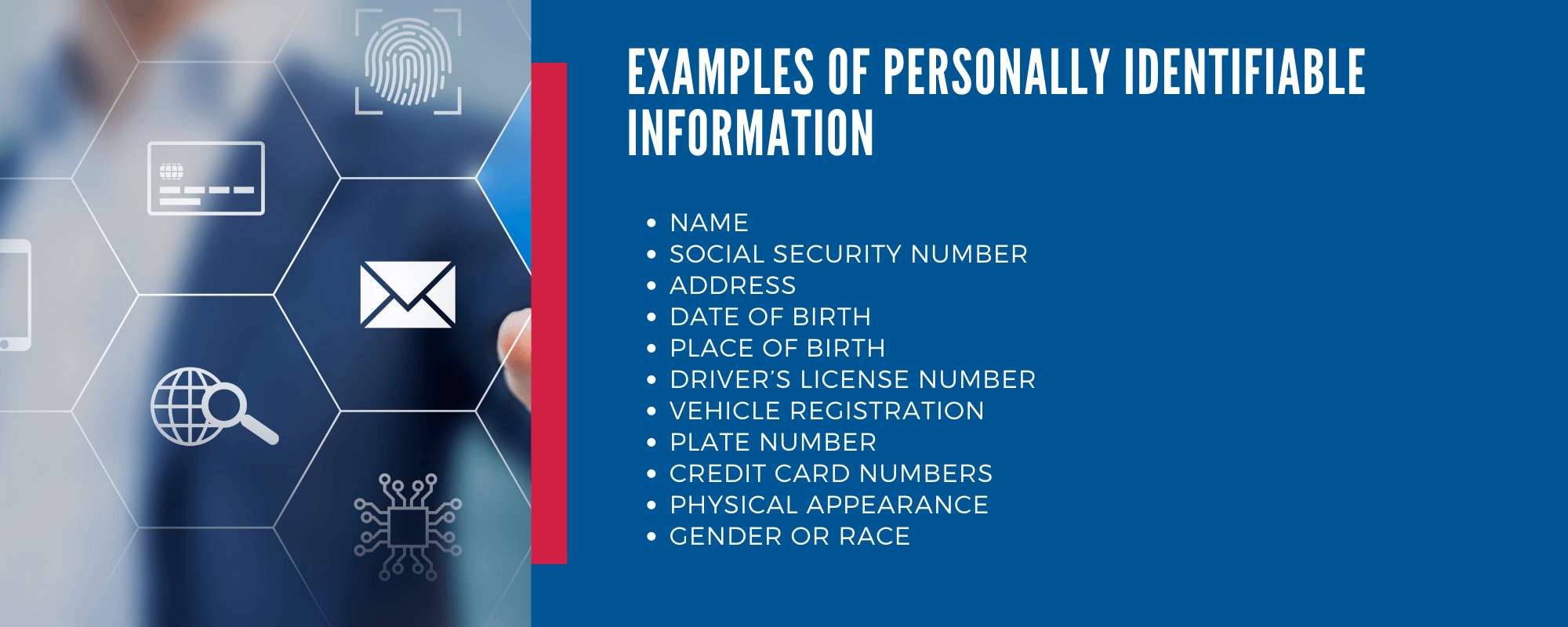
What comprises Personally Identifiable Information?
Anything that can identify you to someone with no direct link to you previously is considered “PII”.
Contacting financial institutions, DMV and Credit Cards is essential to prevent further damage. Your company will want a full report of your personal vulnerabilities. You’ll need to change ALL passwords. Consider adopting security tools such as LastPass which uses random password creators to create highly secure passwords for all sites.
Are you up to date on the latest cyber attacks and other industry news?
To protect their bottom lines, businesses must stay up to date on the evolving threats to their IT infrastructure and data. While the constant stream of information on cyber risks can be overwhelming, Insurance Office of America is here for you.
Cyber Security Planning Guide
Understanding the full scope of your cyber liability is a challenge—one that requires knowledge of various types of breaches, common risks, exposure identification strategies, and mitigation techniques. Our clients can use the IOA Cyber Security Planning Guide, in it you’ll find in-depth information on all of the above, allowing you to better protect your business, information, and customers from cyber threats. Organizations, both large and small, need to be proactive in order to protect against growing cyber threats. Resources like our Cyber Security Planning Guide ensure that, regardless of how you conduct your business, you are doing the due diligence necessary to prepare for your organization’s unique cyber exposures.
Cyber Risk Exposure Scorecard
When data breaches and hacks occur, they can result in devastating damage, such as business disruptions, revenue loss, and legal fees. No organization is immune to the impact of cyber crime, and cyber liability insurance is a crucial part of risk management. Using our Cyber Risk Exposure Scorecard, organizations can assess their level of risk and better determine the level of coverage they need. Want a taste of the full Cyber Scorecard? Take our abbreviated Cyber Assessment here:
Employee Training Materials
The first line of defense against cyber threats is a well-trained workforce. Properly training your employees is one of the easiest ways to prevent a cyber breach from affecting your business. However, because cyber security is a complex topic, thoroughly training all of your employees is not always easy. Simplify the process by using our comprehensive employee training materials. Our clients receive Employee Cyber Training Manuals to educate their workforce regarding common threats and mitigation techniques. These guides cover a range of topics, including communications, devices, and best practices.



